[!Important]
preg_match过滤绕过及RCE重定向截断
0x01#
访问靶场,回显源码
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| <?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-05 20:49:30
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-05 21:32:01
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
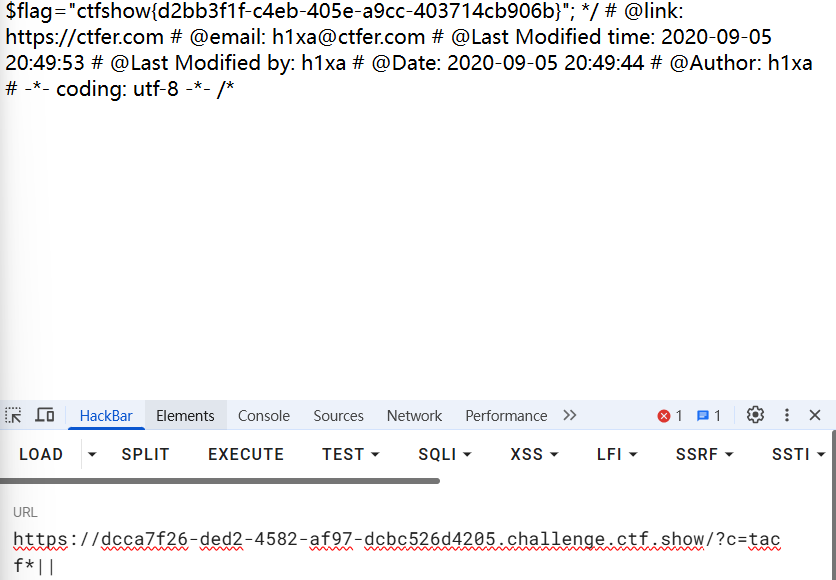
if(isset($_GET['c'])){
$c=$_GET['c'];
if(!preg_match("/;|cat|flag/i", $c)){
system($c." >/dev/null 2>&1");
}
}else{
highlight_file(__FILE__);
}
|
0x02#
[!Note]
代码审计
1
2
3
| if(!preg_match("/;|cat|flag/i", $c)){
system($c." >/dev/null 2>&1");
}
|
preg_match函数过滤; cat flag字段及大小写
>/dev/null 2>&1将输出结果重定向不显示
故构造payload函数思路为绕过preg_match及截断重定向
0x03#
构造payload传参,具体过程与Web42类似,不再赘述